About Caddy
The Ultimate Server
Caddy 2 is a powerful, enterprise-ready, open source web server with automatic HTTPS written in Go
— caddyserver.com
Caddy advertises itself as a simple and reliable web server that's Secure by Default.
About the Vulnerability
The bug bounty hunter Mayank Mukhi (@Hunt2behunter) reported an Open Redirect vulnerability on our website to us. After further analysis for the reason of this vulnerability, it was stated that the Caddy web server in version v2.4.6 is affected by this kind of vulnerability.
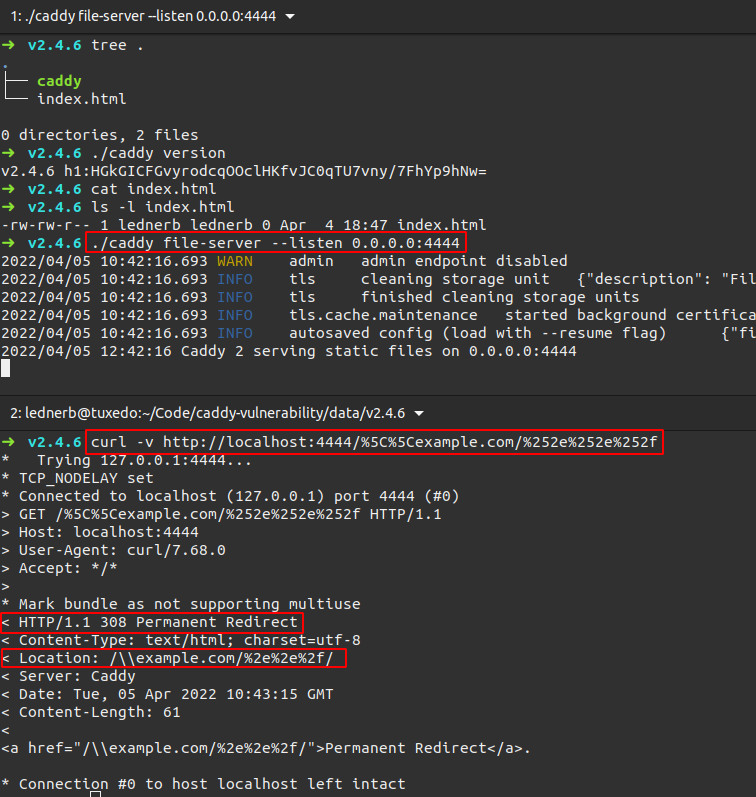
Steps to reproduce
- Download Caddy v2.4.6 from the GitHub Releases page
- Ensure that the file-server's root directory at least contains an index.html file
- Start caddy file-server
- Navigate to the web server with the following path and get a redirect (HTTP Status Code 308):
/%5C%5Cexample.com/%252e%252e%252f
Terminal Screenshot
Vulnerable Versions
All versions v2.x up to v2.5.0-rc.1 were tested and it was confirmed that only version v2.4.6 is affected by the listed attack vector.
Fix
The bug / security issue was fixed in commit 78b5356f2b1945a90de1ef7f2c7669d82098edbd and will be available in the next stable release.
Recommendations
Server administrators should upgrade caddy to the latest version v2.5.0.
Responsible Disclosure Timeline
| Date | Description |
|---|---|
| 2022-04-04 | Mayank Mukhi (@Hunt2behunter) reported an Open Redirect Vulnerability on our site; Vulnerability was confirmed by us; Research started and verified vulnerability in Caddy; Requested CVE-ID from MITRE |
| 2022-04-05 | A tool for automated testing all v2.x caddy versions was developed and used; Confirmed only vulnerable version v2.4.6; Sent a vulnerability report to Matt Holt, Creator, Maintainer and Security Contact for Caddy |
| 2022-04-07 | Matt Holt confirmed that the vulnerability was discovered, reported and fixed months ago; Although no new stable version was released yet |
| 2022-04-21 | Performed additional automated tests to determine commit that fixed the issue |
| 2022-04-22 | Publication of this vulnerability writeup |
| 2022-04-27 | Updated Section Fix with latest caddy release v2.5.0 from 2022-04-25. |
| 2022-05-18 | CVE-2022-28923 was assigned by MITRE for this vulnerability. |
The vulnerability was discovered and reported by:
Sascha Brendel | CEO, IT-Security Consultant & Penetration Tester
![Caddy Open Redirect Vulnerability<br>[CVE-2022-28923]](https://lednerb.de/img/containers/assets/publikationen/header-vulnerability.jpg/c6c9fb0e2aadbf9d0ff0a76fb00cc327/header-vulnerability.jpg)